and businesses consider moving their data to an online
storage service. While the cloud offers a tremendous
amount of storage space at a relatively low cost, the
security of data and the reliability of cloud companies
trigger concerns.
When people register for a cloud computing service,
they sign a written contract or tap or click an online OK
or Agree button to affirm they read and understand the
terms of the agreement. Any data saved on the cloud is
entrusted to the third-party provider, which has a legal
obligation to protect the data from security breaches.
The company also must guard against data loss due to
physical disasters, such as power outages, cooling failures,
and fire. When data has been compromised, many
states require the company to disclose the issue to the
data owner promptly.
who register for the service with a credit card or for
a free trial period and then unleash malware in an
attempt to gain access to passwords. Because the registration
and validation procedure for accessing the cloud
is relatively anonymous, authorities can have difficulty
locating the abusers.
Another concern arises when transferring data over
a network to the cloud. When the data is traveling to
or from a computer and the cloud service, it is subject
to interception. To minimize risk, security experts
emphasize that the web address of the website you are
visiting must begin with https, and the data should be
encrypted and authenticated.
 |
| They point to the USA PATRIOT Act (“Patriot Act”) as the magic wand that allows U.S. law enforcement and national security agencies unrestricted access to any data, anywhere, any time. In fact, the actual impact of the Patriot Act in this cloud context is negligible. |
security issue. Email messages stored on a private
server belong to the company or individual who owns
the computer, so law enforcement officials must obtain
a search warrant to read a particular user’s messages.
In contrast, law enforcement officials can access
email messages stored on the cloud by requesting the
information from the company that owns the cloud
service. The user might not be notified of the search
until up to 90 days after the search occurred; moreover,
the search may occur without limitations and may
include continuous monitoring of an individual’s email
communications.
International laws and industry regulations protect
sensitive and personal data. Germany has some of
the strictest cloud data privacy laws, and, in general,
the European Union’s privacy regulations are more
protective that those in the United States. In much of
Europe, for example, consumers must agree to have
their personal information collected, and they can
review the data for accuracy. The education, health care,
and financial services industries in the United States
have strict data privacy regulations that affect cloud
storage. For example, the Family Educational Rights
and Privacy Act (FERPA) regulates the confidentiality of
students’ educational records, so colleges must obtain
students’ consent to share data with cloud storage
providers and other third parties.
Cloud storage companies have increased their
privacy and security features in recent years. Many
allow consumers and businesses to protect files with
passwords or require two-step authentication to access
files, to delete data if a mobile device has been stolen
or lost, and to delete data that has been stored past an
expiration date.
Consider This: How much of your personal data
is stored on the cloud? Do you have concerns about the
security of this data? Have you ever received a notice
that any of your online data has been compromised?
Should online social networks or email providers give
more explicit notice that data is stored on the cloud?
Should law enforcement officials be able to access your
data without your consent? Why or why not?
Who Is Responsible for Data Left on the Cloud?
Businesses often contract with cloud storage
providers for data storage. Many businesses
also use cloud storage providers to store
customer data. This data could include contact
information, credit card numbers, and
ordering history.
Ownership of cloud data becomes an
issue when a cloud storage provider or the
business using the cloud services closes.
Other issues include what happens if the
business fails to pay the cloud storage
provider, or when a contract ends. Many feel
that it is the responsibility of the business
owner to remove and destroy company
this argument believe that cloud storage
providers should not be accessing data they
host. Others contend that if a business fails
to remove and destroy its data before its
cloud storage contract ends, cloud storage
providers should return the data, or remove
the data permanently.
An ongoing debate exists related to who
is responsible for cloud data security. Many
experts put the responsibility of securing
data in the hands of the data owner. Others
advocate for a shared security model, in
which the cloud storage provider includes
security tools, but the company provides
additional security as needed.
Ownership and security of data should
be included in any contract between
a business and cloud storage provider.
Contracts also should specify what happens
in a variety of scenarios, including if either
party stops its operations, or if hackers
access the data.
Consider This: If a business stops its
operations, who should remove its data
from cloud storage? Why? If a customer
does not remove its data before a contract
ends, should a cloud storage provider return
the data, or can it remove or sell the data?
Why or why not? Who is responsible for
data security? Why?
Hardware Theft, Vandalism, and Failure
Users rely on computers and mobile devices to create, store, and
manage important information. You should take measures to protect computers and devices from
theft, vandalism, and failure.
Hardware theft is the act of stealing digital equipment.
Hardware vandalism involves defacing or destroying digital
equipment. Hardware can fail for a variety of reasons: aging
hardware, natural or man-made disasters, or random events
such as electrical power problems, and even errors in programs
or apps.
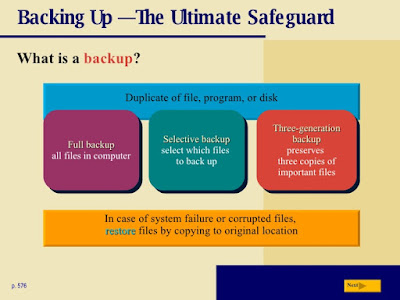
Backing Up — The Ultimate Safeguard
To protect against data loss caused by hardware/software/information theft or system failure,
users should back up computer and mobile device files regularly. As previously described,
a backup is a duplicate of a file, program, or media that can be used if the original is lost,
damaged, or destroyed; and to back up a file means to make a copy of it. In the case of system
failure or the discovery of corrupted files, you restore the files by copying the backed up files to
their original location on the computer or mobile device.
If you choose to back up locally, be sure to use high-quality media. A good choice for a home user
might be optical discs or an external hard drive. Keep your backup media in a fireproof and heatproof
safe or vault, or offsite. Off-site means in a location separate from where you typically
store or use your computer or mobile device. Keeping backup copies off-site minimizes the chance that a single disaster, such as a fire, would destroy both the original and the backup media. An off-site location can be a safe deposit box at a bank, a briefcase, or cloud storage or cloud backup.
Cloud storage provides storage to customers, usually along with synchronization services but often
on smaller amounts of data. By contrast, cloud backup provides only backup and retrieval services,
but generally provides continuous data protection to the cloud. More customers are
opting for cloud backup because it saves them the cost of maintaining hardware.
Various Backup Methods
Business and home users can perform four types of backup:
 | ||||
backup hardware. Files may be
retrieved from anywhere with an
Internet connection on any device.
The only real-time backup. Very fast
recovery of data. Very expensive and requires a great
amount of storage.
Disaster Recovery
A disaster can be natural or man-made (hackers, viruses,
etc.). A disaster recovery plan typically contains these four
components: emergency plan, backup plan, recovery
plan, and test plan.
Emergency Plan:
The emergency plan is organized by type of disaster,
such as fire, flood, or earthquake, and includes:
1. Names and phone numbers of people and
organizations
to notify (company management,
fire and police department, clients, etc.)
2. Computer equipment procedures, such as equipment
or power shutoff, and file removal; employees should
follow these procedures
only if it is safe to do so
3. Employee evacuation procedures
4. Return procedures (who can enter the facility and
what actions they are to perform)
Backup Plan:
The backup plan specifies how
You will use backup files and equipment to
resume computer operations, and includes:
1. The location of backup data, supplies, and equipment
2. Who is responsible for gathering backup resources and
transporting them to an alternate computer facility
3. The methods by which data will be restored from
cloud storage.
4. A schedule indicating the order and approximate
time each application should be up and running.
Recovery Plan:
The recovery plan specifies the actions
you will take to restore full computer operations.
As with the emergency plan, the recovery plan
differs for each type of disaster. We recommend that
you set up planning committees. Each committee
would be responsible for different forms of recovery,
such as replacing hardware or software.
Test Plan:
The test plan includes simulating various levels
of disasters and recording your ability to recover.
You run a test in which the employees follow the steps in
the disaster recovery plan. The test uncovers a few needed
recovery actions not specified in the plan, so you modify the
plan. A few days later, you run another test without giving
the employees any advance notice to test the plan again.
Consider This: For what kinds of natural and
man-made disasters should a company plan? What roles
can cloud storage providers play in helping to recover
from a disaster? How involved should employees be in
developing and testing disaster recovery plans?

































No comments:
Post a Comment