The vast improvements in technology over the past decade have had a distinct impact on
daily life, both at home and at work. Computers have become indispensable tools in our
personal and professional lives, and related technological advancements have changed the
way our everyday items—cars, microwaves, coffeepots, toys, exercise bikes, telephones,
televisions, and more—look and function. As computers and everyday devices become
smarter, they tend to do their intended jobs faster, better, and more reliably than before, as
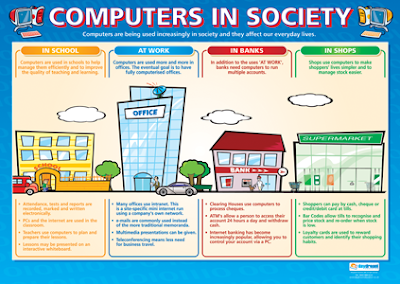
well as take on additional capabilities. In addition to affecting individuals, computerization
and technological advances have changed society as a whole. Without computers,
banks would be overwhelmed by the job of tracking all the transactions they process,
moon exploration and the space shuttle would still belong to science fiction, and some
scientific advances—such as DNA analysis and gene mapping—would be nonexistent. In
addition, we as individuals are getting accustomed to the increased automation of everyday
activities, such as shopping and banking, and we depend on having fast and easy
access to information via the Internet and rapid communications via e-mail and messaging.
In addition, many of us would not think about making a major purchase without
first researching it online. In fact, it is surprising how fast the Internet and its resources
have become an integral part of our society. But despite all its benefits, cyberspace has
some risks. Some of the most important societal implications related to computers and
the Internet are introduced next; many of these issues are covered in more detail in later
chapters of this text.
The benefits of having such a computer-oriented society are numerous,The capability to virtually design, build, and test new buildings, cars, and airplanes before the actual construction begins helps professionals create safer end products.
Technological advances in medicine allow for earlier diagnosis and more effective
treatment of diseases than ever before. The benefit of beginning medical students performing
virtual surgery using a computer instead of performing actual surgery on a patient is
obvious.
The ability to shop, pay bills, research products, participate in online courses, and
look up vast amounts of information 24 hours a day, 7 days a week, 365 days a year via
the Internet is a huge convenience. In addition, a computer-oriented society generates new
opportunities. For example, technologies—such as speech recognition software and Braille input and output devices—enable physically- or visually-challenged individuals to perform necessary
job tasks and to communicate with others more easily.
In general, technology has also made a huge number of tasks in our lives go much faster.
Instead of experiencing a long delay for a credit check, an applicant can get approved for a purchase,
loan, or credit card almost immediately. Documents and photographs can be e-mailed or faxed in mere moments, instead of taking at least a day to be mailed physically.
We can watch many of our favorite TVs shows online, and access up-to-the-minute news at our
convenience. And we can download information, programs,
music files, movies, and more on demand when we want or need
them, instead of having to order them and then wait for delivery
or physically go to a store to purchase the desired items.
Risks of a Computer-Oriented Society
Although there are a great number of benefits from having a computer-oriented society and
a networked economy, there are risks as well. A variety of problems have emerged from our
extensive computer use, ranging from stress and health concerns, to the proliferation of spam
(unsolicited e-mails) and malware (harmful programs that can be installed on our computers
without our knowledge), to security and privacy issues, to legal and ethical dilemmas. Many
of the security and privacy concerns stem from the fact that so much of our personal business
takes place online—or at least ends up as data in a computer database somewhere—and
the potential for misuse of this data is enormous. Another concern is the repercussions of
collecting such vast amounts of information electronically. Some people worry about creating
a “Big Brother” situation, in which the government or another organization is watching
everything that we do. Although the accumulation and distribution of information is a necessary
factor of our networked economy, it is one area of great concern to many individuals.
And some Internet behavior, such as downloading music or movies from an unauthorized
source or viewing pornography on an office computer, can get you arrested or fired.
Security Issues
One of the most common online security risks today is your computer becoming infected with
a malware program, such as a computer virus—a malicious software program designed to
change the way a computer operates. Malware often causes damage to the infected computer,
such as erasing data or bogging down the computer so it does not function well. It can also
be used to try to locate sensitive data on your computer (such as Web site passwords or credit
card numbers) and send that data to the malware creator or to take control of your computer
to use as part of a botnet (a network of computers used without their owners’ knowledge) for
criminal activities. Malware is typically installed by downloading a program that secretly contains
malware or by clicking a link on a Web page or in an e-mail message that then installs
malware. In addition to computers, malware and other security threats are increasingly being
directed toward smartphones and other mobile devices. To help protect your computer or
mobile device, never open an e-mail attachment from someone you do not know or that has
an executable file extension (the last three letters in the file name preceded by a period), such
as .exe, .com, or .vbs, without checking with the sender first to make sure the attachment is
legitimate. You should also be careful about what files you download from the Internet. In
addition, it is crucial to install security software on your computer and mobile devices and to
set up the program to monitor your devices on a continual basis. If a virus
or other type of malware attempts to install itself on your computer or mobile device (such
as through an e-mail message attachment or a Web link), the security program will block it.
If malware does find its way onto your computer or mobile device, the security program will
detect it during a regular scan, notify you, and attempt to remove it.
Privacy Issues
Some individuals view the potential risk to personal privacy as one of the most important
issues regarding our networked society. As more and more data about our everyday activities
is collected and stored on devices accessible via the Internet, our privacy is at risk because
the potential for privacy violations increases. Today, data is collected about practically anything
we buy online or offline, although offline purchases may not be associated with our
identity unless we use a credit card or a membership or loyalty card. At issue is not that
data is collected—with virtually all organizations using computers for record keeping, that is
unavoidable—but rather how the collected data is used and how secure it is. Data collected
by businesses may be used only by that company or, depending on the businesses’ privacy
Security software, Security software is crucial for protecting your computer and mobile devices from
malware and other threats.
Using your primary e-mail address when shopping online or signing up for a sweep-stake or other
online activity will undoubtedly result in spam being sent to that e-mail address. Use a throw-away
e-mail address (a free e-mail address from Gmail or another free e-mail provider that you can
change easily) for these activities instead to help protect your privacy and cut back on the amount of
spam delivered to your regular e-mail account.
Differences in Online Communications
There is no doubt that e-mail and other online communications methods have helped
speed up both personal and business communications and have made them more efficient
(such as avoiding the telephone tag problem). As you spend more and more time
communicating online, you will probably notice some differences between online
communications methods (such as e-mail and social networking updates) and traditional
communications methods (such as telephone calls and written letters). In general,
online communications tend to be much less formal and, in fact, many people
compose and send e-mail messages quickly, without taking the time to reread the message
content or check the spelling or grammar. However, you need to be careful not to
be so casual—particularly in business—that your communications appear unprofessional
or become too personal with people you do not know.
To help in that regard, a special etiquette—referred to as netiquette—has evolved
to guide online behavior. A good rule of thumb is always to be polite and considerate
of others and to refrain from offensive remarks. This holds true whether you are asking
a question via a company’s e-mail address, posting a message on someone’s Facebook
page, or messaging a friend. With business communications, you should also be very
careful with your grammar and spelling to avoid embarrassing yourself. Some specific
guidelines for proper online behavior.
RULE
Use
descriptive
subject lines
EXPLANATION
Use short, descriptive subject lines for e-mail messages and online
posts. For example, "Question regarding MP3 downloads" is much
better than a vague title, such as "Question"
RULE
Don't shout
EXPLANATION
SHOUTING REFERS TO TYPING YOUR ENTIRE E-MAIL MESSAGE
OR ONLINE POST USING CAPITAL LETTERS. Use capital letters only
when it is grammatically correct to do so or for emphasizing a few words.
RULE
Watch what
you say
EXPLANATION
Things that you say or write online can be interpreted as being sexist,
racist, or in just general bad taste. Also check spelling and grammar- typos look unprofessional and nobody likes wading through poorly written materials
RULE
Don't spam your contacts
EXPLANATION
Don't hit Reply All to an e-mail when a simple Reply will do. The same goes for forwarding e-mail chain letters, re-tweeting every joke you run across, or sending every funny YouTube video you find-to everyone you know.
RULE
Be cautious
EXPLANATION
Don't give out personal information-such as your real name, telephone number, or credit card information-to people you meet online.
RULE
Think before
you send or post
EXPLANATION
Once you send an e-mail or text message or post something online, you lose control of it. Don't include content (such as compromising photos of yourself) that you would not want shared with others, and don't tag people in photos that are unflattering to them. In addition, don't e-mail or post anything if emotions are running high-wait until you calm down
Another trend in online communications
is the use of abbreviations
and emoticons. Abbreviations
or acronyms, such as BTW for “by
the way,” are commonly used to save
time in all types of communications
today. They are being used with
increased frequency in text messaging
and e-mail exchanged via mobile
phones to speed up the text entry
process. Emoticons are illustrations
of faces showing smiles, frowns, and
other expressions that are created
with keyboard symbols—such as
the popular :-) smile emoticon—and
allow people to add an emotional
tone to written online communications.
Without these symbols, it is
sometimes difficult to tell if the person
who sent the online communication
is serious or joking because
you cannot see the individual’s face
or hear his or her tone of voice.
While most people would agree that using abbreviations and emoticons with personal
communications is fine, they are not usually viewed as appropriate for formal business
communications.
The Anonymity Factor
By their very nature, online communications lend themselves to anonymity. Because recipients
usually do not hear senders’ voices or see their handwriting, it is difficult to know for
sure who the sender is. Particularly on forums (online discussions in which users post messages
and respond to other posts), in virtual worlds (online worlds that users can explore),
and other online activities where individuals use made-up names instead of real names,
there is an anonymous feel to being online.
Being anonymous gives many individuals a sense of freedom, which makes them feel
able to say or do anything online. This sense of true freedom of speech can be beneficial.
For example, a reserved individual who might never complain about a poor product or service
in person may feel comfortable lodging a complaint by e-mail. In online discussions,
many people feel they can be completely honest about what they think and can introduce
new ideas and points of view without inhibition. Anonymous e-mail is also a safe way for
an employee to blow the whistle on a questionable business practice, or for an individual to
tip off police to a crime or potential terrorist attack.
But, like all good things, online anonymity can be abused. Using the Internet as their
shield, some people use rude comments, ridicule, profanity, and even slander to attack people,
places, and things they do not like or agree with. Others may use multiple online identities
(such as multiple usernames on a message board) to give the appearance of increased
support for their points of view. Still others may use multiple identities to try to manipulate
stock prices (by posting false information about a company to drive the price down, for
instance), to get buyers to trust an online auction seller (by posting fictitious positive feedback
about themselves), or to commit other illegal or unethical acts.
It is possible to hide your true identity while browsing or sending e-mail by removing
personal information from your browser and e-mail program or by using privacy software that
acts as a middleman between you and Web sites and hides your identity, as discussed in more
detail in Chapter 5. But, in fact, even when personal information is removed, ISPs and the
government may still be able to trace communications back to a particular
computer when a crime has occurred, so it is difficult—perhaps impossible—
to be completely anonymous online.
Information Integrity
The Web contains a vast amount of information on a wide variety of topics.
While much of the information is factual, other information may be
misleading, biased, or just plain wrong. As more and more people turn to
the Web for information, it is crucial that they take the time to determine
if the information they obtain and pass on to others is accurate. There have
been numerous cases of information intended as a joke being restated on
a Web site as fact, statements being quoted out of context (which changed
the meaning from the original intent), and hoaxes circulated via e-mail.
Consequently, use common sense when evaluating what you read online,
and double-check information before passing it on to others.
One way to evaluate online content is by its source. If you obtain
information from a news source that you trust, you should feel confident
that the accuracy of its online information is close to that of its offline
counterpart. For information about a particular product, go to the originating
company. For government information, government Web sites are your
best source for fact checking. There are also independent Web sites (such
as the Snopes Web site shown above that report on the validity of
current online rumors and stories.
Snopes.com. This
Web site can be used
to check out online
rumors.































No comments:
Post a Comment